analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
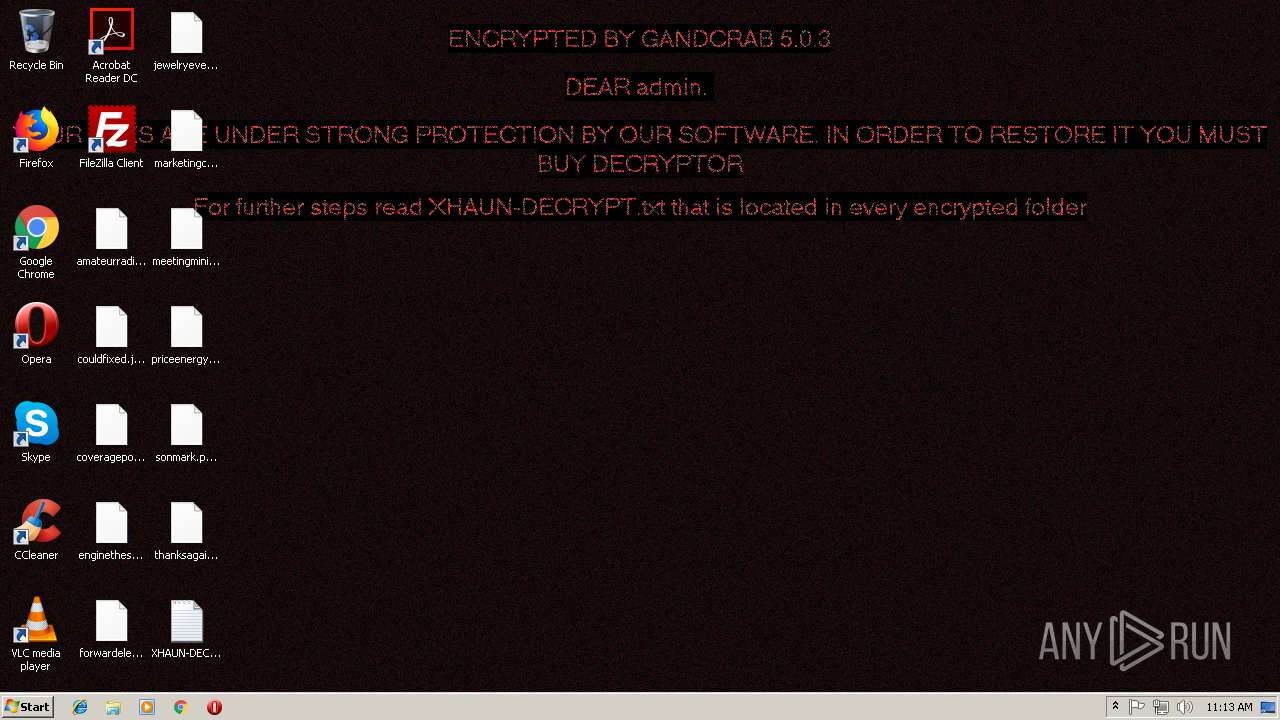
| File name: | GandCrab 5.0.3 downloader.js |
| Full analysis: | https://app.any.run/tasks/5c1bed7b-40e0-4619-b6a5-5cc89a754c27 |
| Verdict: | Malicious activity |
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | October 10, 2018 at 10:13:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 595A31A4913951D3EB7211618AE75DEA |
| SHA1: | 16DBFE657AC36A8D84AF411F13EBFF1CCC5E56AD |
| SHA256: | BE6A4997FDF6EA0D74A973AE0A361EBCC4CBBC74A5801E75A76BB52A2B424E34 |
| SSDEEP: | 12288:lNelh1RLsMUu8HRCTEr45VYYtkG8eAVIsNOd:lNelh1RLsMUu8HRCR3UeAVIsNs |
MALICIOUS
Application was dropped or rewritten from another process
- dsoyaltj.exe (PID: 3420)
Actions looks like stealing of personal data
- wermgr.exe (PID: 2772)
GandCrab keys found
- wermgr.exe (PID: 2772)
Writes file to Word startup folder
- wermgr.exe (PID: 2772)
Dropped file may contain instructions of ransomware
- wermgr.exe (PID: 2772)
Renames files like Ransomware
- wermgr.exe (PID: 2772)
Deletes shadow copies
- wermgr.exe (PID: 2772)
SUSPICIOUS
Executable content was dropped or overwritten
- WScript.exe (PID: 2816)
Creates files like Ransomware instruction
- wermgr.exe (PID: 2772)
Reads Internet Cache Settings
- wermgr.exe (PID: 2772)
Starts CMD.EXE for commands execution
- wermgr.exe (PID: 2772)
Creates files in the user directory
- wermgr.exe (PID: 2772)
INFO
Dropped object may contain TOR URL's
- wermgr.exe (PID: 2772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2816 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\GandCrab 5.0.3 downloader.js" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\dsoyaltj.exe" | C:\Users\admin\dsoyaltj.exe | — | WScript.exe | |||||||||||
User: admin Company: www.sopcast.com Integrity Level: MEDIUM Description: SopCast Main Application Exit code: 0 Version: 4.2.0.800 Modules
| |||||||||||||||
| 2772 | "C:\Windows\System32\wermgr.exe" | C:\Windows\System32\wermgr.exe | dsoyaltj.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 116 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | wermgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3432 | "C:\Windows\System32\cmd.exe" /c timeout -c 5 & del "C:\Windows\System32\wermgr.exe" /f /q | C:\Windows\System32\cmd.exe | — | wermgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3888 | timeout -c 5 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
568
Read events
533
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2816) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2816) WScript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E0078006800610075006E000000 | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A40000525341310008000001000100B5B6DF4755F8851F0F3345FD77E8E92425FE5B041E526F201237F099AC99A49091C5207C4A520E426BAEA83CE5B8E2501B914DAE7F11BE92271DCC7C8C9215E90AEFA9AA7070E04E0D2DA1B3B30088359BB2EDE43BAE52FED2626D7A9FE44C04CF7367854CC36197D4CCE92E4CA9C46DB3DE2B8D2AFD9A06EB6116BFB929A148051B9832DFD5A7FB2B0B6DC3B94A728BDD351663F0F61E13D16E8FE9C4D51CED12DBDE6E8E10AA24B65F876BF05D5D11B55C95C1612A4EC46C30C14DBC628FCD56E3EFFE9357D737CEF39EB528F2D8C88A0E99DBD2F71820717663725CE20B70402B653C67D85E3A5D4D78FCE740628CE6CE4F99830527F7F04809BB4FB18EEE | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\keys_data\data |
| Operation: | write | Name: | private |
Value: 9404000066703A0D6315579762A7879F77BAC972D702C4CAD3CADB9BBDF6172EE50D204B8D870B151374C796ED8DD953DB8E4B97C7DE9125B87C3D57ABF0D9685A20FA2004CB61FA4781EE91C26F00B779FB9EF9957C65BBE08F689405ADC45CEAEB07FB7B606B2619AC1A667EC0D2ABBDAD773D56FEF238F3DB12BEB7026FFC85AF80E3AFA3796A807EBAC46EF676C306E04A7CDD1DC8AD30AB3BCD5F27E84F8F16A1EF1F224B5CB02313F123A5F1B908AF72BBD38C7770F12A0E92DC970F30093AFC1F938AA0FCD2CC05044C66781A51A1B55B70A31B5125CC9CBFF04F45826B75791C4936AFB7ED1599D52FA4CD7F98AD6B50FEC9D5948AA30969A2E856421BDC5203E58602AD6F2E3FB733A81F4A5FB5D387F8C181ECA4D0AB3BB698295D52C22D2D4FAC03A0D41E454A8991E6CB8DFD9FB6C9C6ACC16C43A6529964B7AD50C1BBD390A3B0F83B4789C9505C1D83CB2CC59602921FED79EC89F18213CA3199A255C78E2EEF13A5E09C66FFFBB3A894B986DDAA0A4577524CF2A07DBA549FB88CF3EEDCD026F8919A540BD37E0B52740619BF36DF77EF60D54E4D9FD2A054A7297F500C27E1F35E85FE11583F2E229BEF8355FA242F5D1DE538E07329BE4C919D13BBD524F40536F244086EC5050CDDE4C973687A2B28A1E4E6ADFAC3B35C206D6D36DC750D9F892E22EF466A2D7DC69D2C31E784C79099ADB8267F093F3BF080D259DAA7928A28ACD48CB2B1AD5F41A953CAD1AC9ED2398E2E446D66DA7AA2100277E6E6F08523EB64AE532AD39E05A4CC7FCD50982369966A6B4457FC1F9FBDADBFF5DB684FABE98C8CE3F7DC82701560D4B7A0F5CE4C4D093120254B01380AB2618931F1A1A5273FD77F7A011808A9DBCCFBC89B0169CAB92295FEF9F88278869D64386C6DFA9C9C11990997056F6DDE918D264ABFB0735EEAC0F76D3193B51C0F62DCF0DFEA383DE2BFE4A54A49C71AB187D14239878EE48DC0DE3C331089DCB9B55F59F744E4E319B1DF257EC8D24437F678CA8BC6D99026A435ADF19FAB7185A61C17D8765D6B94268429D23EB6B81D6332082D11A4A320FFE40D37839B7A98D63320FE755B97C1807D2AA454984CA402BED7B52D7ED65D7D11397E21FF313C000FCADF1DA9EF7DCEAE8F15B3750BB03ED852F94B5CCEE0308E6A0673680DE4AFCFD833D3EBC3E40CA079E963AB52246B2FE1E6DB4B4330544625D11787A200CBF5EA815E9E38E3D339F885D5526411354A7D4F1D26CDC2F17402DC988BBB1FF2307FC82D3B973DFFD54CB4FF7E5A33441FE297F926C23E5E792D522177E8DC046AD07D6BAC61BAC69FF5E4DF35D039E09019842160C3F346722CCE75AFFC153D832AC062B4F0C89F2C7A41A07F498D0ACE51CC30BD65C777AC090082AC30FDBBC5D3E55CC3BAFD2E0D6A6532337916799CE8F627119A99F9520E3014984A05264839ADB494C191B2CEAAC993FF24C91B2E3AAE35394C9838A8026B1DAF2E05888F050CFFC80116082BFACF90AFABE0128C16E9A3A5AEDC694E2DA6622020040F3E51D313B89B6D55B46AA5A18D25FD96519152CCE3EF9EBEA343784D5EC2E863C32240D3F7D8018B0D36F8C642E2D0AB52508E1C11ACF40DFDA95856EB8798A09101A9AE35A6674BD40EBCBD15CEBFEA876AB9A4FAA7C04EAE65B3FA8558682C7D276812F712BF8605A1F957952463FFA65D0940A986D271AF229D9E955FB1FAE050C2A590CE277086F3845DFE6E51ADF2BA627FE4E5488B0EFD354655DBED554157350F11FA3CD368F4A045FAC4828C080D06D11B11B7093794D6C2B293A079E97B7865487DE2F2DF7C1FC36E486AE755CF702B2742AC5581EE30994316DF79F3FD35802C4F7F253BCC97E3962BA7CA61E16B3340C459500E891F1685E6EE4D311F17B7C4C5D4FE66FD69593ED292CE878EA724FFC110AACD9DB6E9C5BE3420E071442667347B155F5B6B7D7DD68C9FEB2BED2F33470BF8E1A1C0926A7B7C4BD3A6ACA86C1C0FAB8447A0B7A15DA32E7A3A56F927F95D06C7FAB0B45531CA68311305EA15887630C8A73AF80964EE77DD0CD09B23C8DF429DEA285E709345D48E1AB27025808AE7FC326BC8B69868308D3D7B1C409C2FFAA0207ED48A8AB9D20A71F13BFD91FB594716BB0CC7D4DF3FB9907FED4A673E897C527848BD588DFE2C1AA04A632D646355FA997B2D354FD13736043DD9B645B164E3EA042E881C7C4FB0399C92E8BDCBF971C998B0B149C0C05F24D58F39C056DE49380E5690946E190D232724259E3C743D577B946ECD67EE926668B43C11B716A442A9BD5DE1549A867A214146CF64B2E0395C243958909FD386F247FAA6DD8989CB930AC6C0E183E36E8BEBD020301628A67D29E701F60109C0 | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wermgr_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wermgr_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2772) wermgr.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\wermgr_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
1
Suspicious files
265
Text files
221
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3420 | dsoyaltj.exe | C:\Users\admin\AppData\Local\Temp\Liebert.bmp | — | |
MD5:— | SHA256:— | |||
| 2772 | wermgr.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 2772 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 2772 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 2772 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 2772 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 2772 | wermgr.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
| 2772 | wermgr.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\XHAUN-DECRYPT.txt | text | |
MD5:7D10EC9B55C69E9C43B68C98D05025DE | SHA256:BACAC2216C222B7D430760FE0F54A7A864FCC6097B184D199C1B0418ABF9C8D8 | |||
| 2772 | wermgr.exe | C:\Users\admin\XHAUN-DECRYPT.txt | text | |
MD5:7D10EC9B55C69E9C43B68C98D05025DE | SHA256:BACAC2216C222B7D430760FE0F54A7A864FCC6097B184D199C1B0418ABF9C8D8 | |||
| 2772 | wermgr.exe | C:\Users\admin\.oracle_jre_usage\XHAUN-DECRYPT.txt | text | |
MD5:7D10EC9B55C69E9C43B68C98D05025DE | SHA256:BACAC2216C222B7D430760FE0F54A7A864FCC6097B184D199C1B0418ABF9C8D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
127
TCP/UDP connections
119
DNS requests
110
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2772 | wermgr.exe | POST | 510 | 78.46.98.73:443 | https://www.2mmotorsport.biz/content/imgs/imzuim.gif | DE | html | 757 b | unknown |
2772 | wermgr.exe | POST | 404 | 217.26.53.161:443 | https://www.haargenau.biz/content/assets/soamzukamo.png | CH | xml | 981 b | malicious |
2772 | wermgr.exe | POST | 510 | 136.243.13.215:443 | https://www.holzbock.biz/data/images/sezu.png | DE | html | 740 b | suspicious |
2772 | wermgr.exe | POST | 404 | 83.138.82.107:443 | https://www.swisswellness.com/uploads/tmp/seessesoso.jpg | DE | html | 14.7 Kb | whitelisted |
2772 | wermgr.exe | POST | 404 | 46.30.45.85:443 | https://www.fliptray.biz/content/pictures/ruesfu.jpg | RU | html | 604 b | malicious |
2772 | wermgr.exe | POST | 404 | 192.185.159.253:443 | https://www.pizcam.com/wp-content/tmp/sodake.jpg | US | html | 22.7 Kb | malicious |
2772 | wermgr.exe | POST | — | 212.59.186.61:443 | https://www.hotelweisshorn.com/includes/pics/kemezumo.jpg | CH | — | — | malicious |
2772 | wermgr.exe | POST | 404 | 83.166.138.7:443 | https://www.whitepod.com/wp-content/pics/kemeesdade.gif | CH | html | 109 Kb | whitelisted |
2772 | wermgr.exe | POST | 404 | 104.24.23.22:443 | https://www.belvedere-locarno.com/wp-content/images/keesdekemo.jpg | US | html | 16.1 Kb | shared |
2772 | wermgr.exe | POST | 404 | 80.244.187.247:443 | https://www.hotelfarinet.com/content/pictures/darues.png | GB | html | 20.1 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2772 | wermgr.exe | 78.46.98.73:443 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | unknown |
2772 | wermgr.exe | 217.26.53.161:443 | www.haargenau.biz | Hostpoint AG | CH | malicious |
2772 | wermgr.exe | 136.243.13.215:443 | www.holzbock.biz | Hetzner Online GmbH | DE | suspicious |
2772 | wermgr.exe | 74.220.215.73:443 | www.bizziniinfissi.com | Unified Layer | US | malicious |
2772 | wermgr.exe | 192.185.159.253:443 | www.pizcam.com | CyrusOne LLC | US | malicious |
2772 | wermgr.exe | 46.30.45.85:443 | www.fliptray.biz | Webzilla B.V. | RU | suspicious |
2772 | wermgr.exe | 83.138.82.107:443 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
2772 | wermgr.exe | 212.59.186.61:443 | www.hotelweisshorn.com | green.ch AG | CH | malicious |
2772 | wermgr.exe | 83.166.138.7:443 | www.whitepod.com | Infomaniak Network SA | CH | malicious |
2772 | wermgr.exe | 104.24.23.22:443 | www.belvedere-locarno.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
www.hardrockhoteldavos.com |
| whitelisted |